Using exists cer.key to access HTTPS via Self-signed cert
Write by mane. Reproduction is not allowed (禁止轉載) !!!
Introduction
Some web servers NEED to verify the HTTPS certificate to allow access to the service, In pentester, if you get the ca.key file, you can self-signed to access the https service, because you can download ca.crt which include public key in HTTPS server.
Private key is not allowed to be leaked, attacker can use this private key to generate new self-signed certificate and sign it in firefox, the firefox need to import PKCS#12 certificate.
In general, to generate PKCS#12 to firefox, you need to obtain two files whose ca.ket and ca.crt.
A Private Key
Here have a example, Assuming you have obtained a ca.key file.
$cat ca.key
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDPczpU3s4Pmwdb
7MJsi//m8mm5rEkXcDmratVAk2pTWwWxudo/FFsWAC1zyFV4w2KLacIU7w8Yaz0/
2m+jLx7wNH2SwFBjJeo5lnz+ux3HB+NhWC/5rdRsk07h71J3dvwYv7hcjPNKLcRl
uXt2Ww6GXj4oHhwziE2ETkHgrxQp7jB8pL96SDIJFNEQ1Wqp3eLNnPPbfbLLMW8M
YQ4UlXOaGUdXKmqx9L2spRURI8dzNoRCV3eS6lWu3+YGrC4p732yW5DM5Go7XEyp
s2BvnlkPrq9AFKQ3Y/AF6JE8FE1d+daVrcaRpu6Sm73FH2j6Xu63Xc9d1D989+Us
PCe7nAxnAgMBAAECggEAagfyQ5jR58YMX97GjSaNeKRkh4NYpIM25renIed3C/3V
Dj75Hw6vc7JJiQlXLm9nOeynR33c0FVXrABg2R5niMy7djuXmuWxLxgM8UIAeU89
1+50LwC7N3efdPmWw/rr5VZwy9U7MKnt3TSNtzPZW7JlwKmLLoe3Xy2EnGvAOaFZ
/CAhn5+pxKVw5c2e1Syj9K23/BW6l3rQHBixq9Ir4/QCoDGEbZL17InuVyUQcrb+
q0rLBKoXObe5esfBjQGHOdHnKPlLYyZCREQ8hclLMWlzgDLvA/8pxHMxkOW8k3Mr
uaug9prjnu6nJ3v1ul42NqLgARMMmHejUPry/d4oYQKBgQDzB/gDfr1R5a2phBVd
I0wlpDHVpi+K1JMZkayRVHh+sCg2NAIQgapvdrdxfNOmhP9+k3ue3BhfUweIL9Og
7MrBhZIRJJMT4yx/2lIeiA1+oEwNdYlJKtlGOFE+T1npgCCGD4hpB+nXTu9Xw2bE
G3uK1h6Vm12IyrRMgl/OAAZwEQKBgQDahTByV3DpOwBWC3Vfk6wqZKxLrMBxtDmn
sqBjrd8pbpXRqj6zqIydjwSJaTLeY6Fq9XysI8U9C6U6sAkd+0PG6uhxdW4++mDH
CTbdwePMFbQb7aKiDFGTZ+xuL0qvHuFx3o0pH8jT91C75E30FRjGquxv+75hMi6Y
sm7+mvMs9wKBgQCLJ3Pt5GLYgs818cgdxTkzkFlsgLRWJLN5f3y01g4MVCciKhNI
ikYhfnM5CwVRInP8cMvmwRU/d5Ynd2MQkKTju+xP3oZMa9Yt+r7sdnBrobMKPdN2
zo8L8vEp4VuVJGT6/efYY8yUGMFYmiy8exP5AfMPLJ+Y1J/58uiSVldZUQKBgBM/
ukXIOBUDcoMh3UP/ESJm3dqIrCcX9iA0lvZQ4aCXsjDW61EOHtzeNUsZbjay1gxC
9amAOSaoePSTfyoZ8R17oeAktQJtMcs2n5OnObbHjqcLJtFZfnIarHQETHLiqH9M
WGjv+NPbLExwzwEaPqV5dvxiU6HiNsKSrT5WTed/AoGBAJ11zeAXtmZeuQ95eFbM
7b75PUQYxXRrVNluzvwdHmZEnQsKucXJ6uZG9skiqDlslhYmdaOOmQajW3yS4TsR
aRklful5+Z60JV/5t2Wt9gyHYZ6SYMzApUanVXaWCCNVoeq+yvzId0st2DRl83Vc
53udBEzjt3WPqYGkkDknVhjD
-----END PRIVATE KEY-----
A Public Cert (X.509 PEM file)
If there is a server running an HTTPS server, you can use firefox to access and export the public crt file like here:
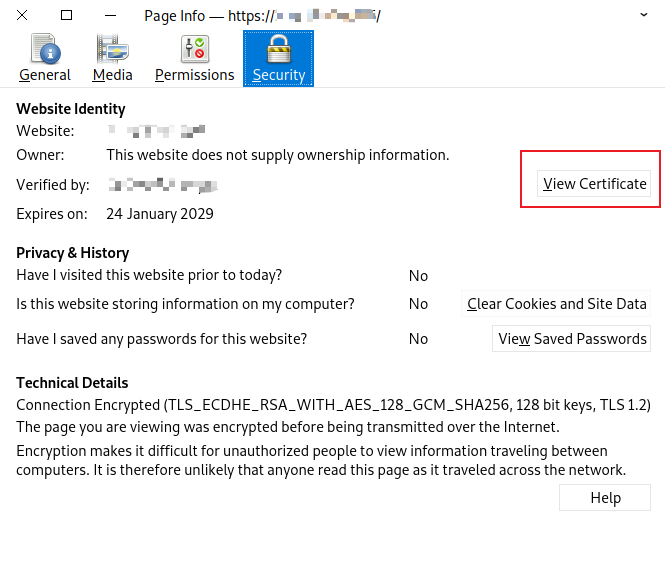
In new windows, just click PEM to download X.509 PEM file.
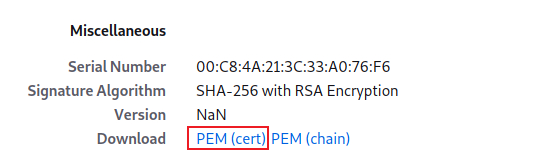
and save it in ca.crt.
Checking your private key and public cert match or not
Now you need to check if your private key's public key and public cert's public key match.
$openssl pkey -in ca.key -pubout
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAz3M6VN7OD5sHW+zCbIv/
5vJpuaxJF3A5q2rVQJNqU1sFsbnaPxRbFgAtc8hVeMNii2nCFO8PGGs9P9pvoy8e
8DR9ksBQYyXqOZZ8/rsdxwfjYVgv+a3UbJNO4e9Sd3b8GL+4XIzzSi3EZbl7dlsO
hl4+KB4cM4hNhE5B4K8UKe4wfKS/ekgyCRTRENVqqd3izZzz232yyzFvDGEOFJVz
mhlHVypqsfS9rKUVESPHczaEQld3kupVrt/mBqwuKe99sluQzORqO1xMqbNgb55Z
D66vQBSkN2PwBeiRPBRNXfnWla3Gkabukpu9xR9o+l7ut13PXdQ/fPflLDwnu5wM
ZwIDAQAB
-----END PUBLIC KEY-----
$openssl x509 -in ca.crt -pubkey -noout
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAz3M6VN7OD5sHW+zCbIv/
5vJpuaxJF3A5q2rVQJNqU1sFsbnaPxRbFgAtc8hVeMNii2nCFO8PGGs9P9pvoy8e
8DR9ksBQYyXqOZZ8/rsdxwfjYVgv+a3UbJNO4e9Sd3b8GL+4XIzzSi3EZbl7dlsO
hl4+KB4cM4hNhE5B4K8UKe4wfKS/ekgyCRTRENVqqd3izZzz232yyzFvDGEOFJVz
mhlHVypqsfS9rKUVESPHczaEQld3kupVrt/mBqwuKe99sluQzORqO1xMqbNgb55Z
D66vQBSkN2PwBeiRPBRNXfnWla3Gkabukpu9xR9o+l7ut13PXdQ/fPflLDwnu5wM
ZwIDAQAB
-----END PUBLIC KEY-----
If they do not match, the following steps will not work.
Generate RSA (client.key)
Generate RSA for Certificate Signing Request use.
$openssl genrsa -out client.key 4096
Generating RSA private key, 4096 bit long modulus (2 primes)
...................................................................................................................++++
.................................................................................................................................................................++++
e is 65537 (0x010001)
Now you get client.key.
Generate Certificate Signing Request (client.csr)
$openssl req -new -key client.key -out client.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:Macau
Locality Name (eg, city) []:Macau
Organization Name (eg, company) [Internet Widgits Pty Ltd]:manesec
Organizational Unit Name (eg, section) []:manesec
Common Name (e.g. server FQDN or YOUR name) []:mane
Email Address []:mane@manesec.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Now you get client.csr.
Generate to digital certificate .cer file
$openssl x509 -req -in client.csr -CA ca.crt -CAkey ca.key \
-set_serial 9001 -extensions client -days 9002 -outform PEM \
-out client.cer
Signature ok
subject=C = CN, ST = Macau, L = Macau, O = manesec, OU = manesec, CN = mane, emailAddress = mane@manesec.com
Getting CA Private Key
Now you get client.cer.
The total you will get:
$ll
total 20K
-rw-r--r-- 1 mane mane 1.1K Oct 5 07:23 ca.crt
-rw-r--r-- 1 mane mane 1.7K Oct 5 06:05 ca.key
-rw-r--r-- 1 mane mane 1.5K Oct 5 07:44 client.cer
-rw-r--r-- 1 mane mane 1.7K Oct 5 07:37 client.csr
-rw------- 1 mane mane 3.2K Oct 5 07:35 client.key
Convert it to PKCS#12
Firefox only suppory to import PKCS#12 file, so it's time to generate PKCS#12 file.
$openssl pkcs12 -export -inkey client.key -in client.cer -out client.p12
Enter Export Password:
Verifying - Enter Export Password:
Now you get client.p12.
Time to import certificate to firefox
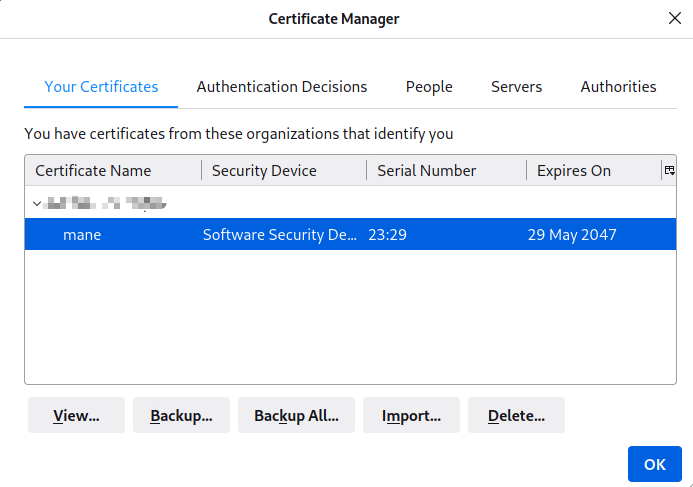
Using client.p12 import to firefox.
Using ca.crt import to firefox.
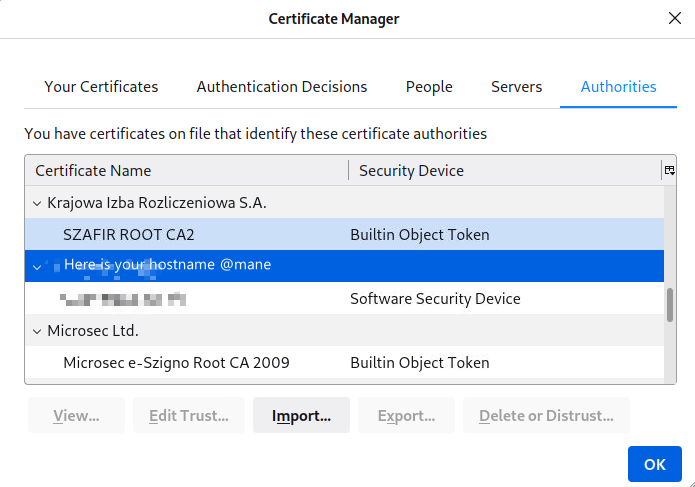
Now you only need to access the HTTPS server with domain name, it will be failed through the ip access.
Problems encountered
If the server still fails, please try again after resetting the cookie, history and cert.
Conclusion
No conclusion, Mane lazy to write, more of information need to google to understanding it.
Reference
Firefox 54 Stopped Trusting Self-Signed Certs
Comments
Post a Comment