通過ADCS申請證書並連接 winrm over https
禁止轉載,可以引用來源,by mane。
Introduction
下面介紹如何通過ADCS申請證書,然後連接到SSL版本的Winrm(端口是5986)。
環境:需要一個AD環境,一個有權限通過Winrm登錄的賬號,這個賬號可以通過ADCS申請證書,且AD只允許5986去登錄。
Quick to find ADCS service if installed
從兩個地方可以快速判斷到AD有沒有開啓ADCS,第一種方法是利用smb看看有沒有CertEnroll這個文件夾:
$smbmap -u amanda -p 'Ashare1972' -H 10.129.190.139
[+] IP: 10.129.190.139:445 Name: 10.129.190.139
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
CertEnroll READ ONLY Active Directory Certificate Services share
Department Shares READ ONLY
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
Operations NO ACCESS
SYSVOL READ ONLY Logon server share
第二種方法是使用瀏覽器看看有沒有 http://<IP>/certsrv, 如果有提示要求輸入賬號密碼就説明AD提供了ADCS服務。
注意:gobuster需要增加狀態碼 401 才可以掃出來。
Winrm Failed need to Winrm over https
使用5985端口連接winrm失敗,失敗信息如下:
$evil-winrm -u amanda -p 'Ashare1972' -i 10.129.190.139
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMHTTPTransportError happened, message is Unable to parse authorization header. Headers: {"Server"=>"Microsoft-HTTPAPI/2.0", "Date"=>"Thu, 29 Dec 2022 05:52:45 GMT", "Connection"=>"close", "Content-Length"=>"0"}
Body: (401).
Error: Exiting with code 1
所以下面嘗試申請證書使用winrm over https去連接。
Apply The Certificate
只允許WINRM的HTTPS鏈接,這是因爲由AD的GPO設定的(參考這裏),由於安全的考慮,AD硬性要求使用https的winrm,恰巧ADCS服務有開,可以嘗試向ADCS去申請證書。
要連接winrm over https,則需要準備兩個文件,Private key file 和 Certificate Require file.
# 首先生成一個 private key
$openssl genrsa -aes256 -out amanda.key 2048
Generating RSA private key, 2048 bit long modulus (2 primes)
.............................................+++++
....................+++++
e is 65537 (0x010001)
Enter pass phrase for amanda.key:
Verifying - Enter pass phrase for amanda.key:
# 然後申請證書請求
$openssl req -new -key amanda.key -out amanda.csr
Enter pass phrase for amanda.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:
State or Province Name (full name) [Some-State]:
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
# 申請證書請求如下
$cat amanda.csr
-----BEGIN CERTIFICATE REQUEST-----
MIICijCCAXICAQAwRTELMAkGA1UEBhMCQVUxEzARBgNVBAgMClNvbWUtU3RhdGUx
ITAfBgNVBAoMGEludGVybmV0IFdpZGdpdHMgUHR5IEx0ZDCCASIwDQYJKoZIhvcN
AQEBBQADggEPADCCAQoCggEBAMksr0vQNce6AEl7gizvUtPQlehxWanMTCdgfhIz
bPWlVVQ3SPDXjAV1T1OgBwI7Oa0BDiTenxmbwpZv6wwrnhgn5VsPMFkwhRa5HBDv
LGfL99HCfDnAtQ5DlRx/WBU/4Fr9sBitQjVad5c5Z35gnZCuRLVJ1kbUHQajaX+X
VVr7VuKdkOW7Qv7eH/WzAaHUllCNTHaBHEuxpP9CCIzU5OkR9H5Q13FWkQC1VqT2
KvxUGvQnigQAgRjFci1J9MzMVal8fDviPEtCHC4Itu9zy9EUovMsNvB+aH484SkW
x9xzH010bTRdVi+1N4Telm0yYydDLwmBz/u4y6zMSXcIf2ECAwEAAaAAMA0GCSqG
SIb3DQEBCwUAA4IBAQALgZ295VIQZBhcwJR2o9EqS395gCGHVSuHnSy9dWdXOgoi
ZoYLBkws3cdB0Zwj6OAoI+Lm4+cUQjzp3+AZudEQc4aBewCbuTRe8B4YlbcAzSJR
AtKkxOQP0ZoC979U6qV6baIlNG6WBwrDyJ9TGH5IfMF0Or4N3/T6toYldPB/q3rf
F0lPG4oBQyJ7gd8AcRZNBV9JjNVdGv4ShELfUH2tTUGMrtBOqXd1X4C83tWJHAnM
U39vA0gTqrbvor2EhMX4pIecgzs0T5XXde8G5lo0NPfv4jdlbi6a/6z0xCaYOYB4
HUhj3TnAcpw/p/J4tW6PMd4xXX4A5NlFzrFA1Uaw
-----END CERTIFICATE REQUEST-----
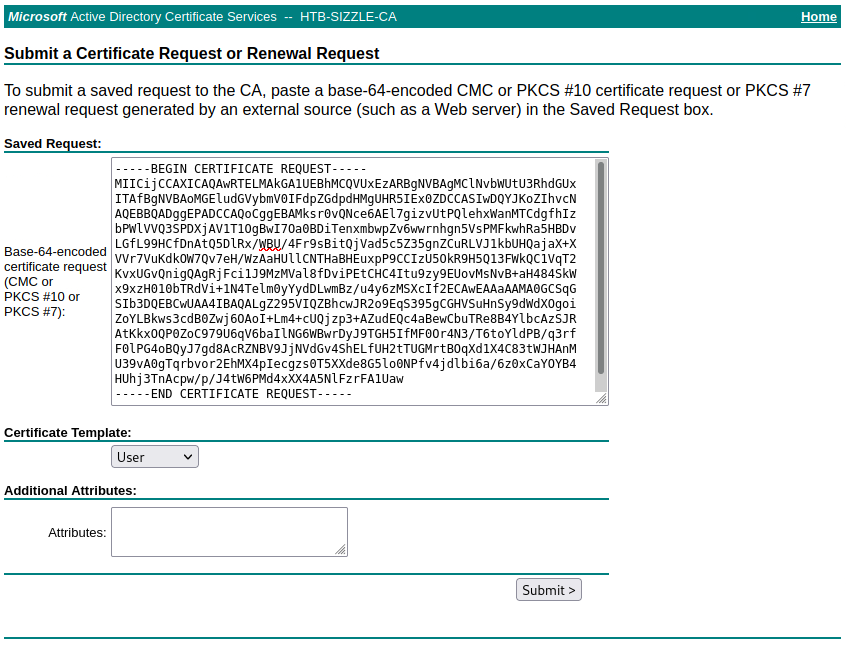
從WEB中申請證書,只需要複製.csr内容到web界面,然後提交就可以了。
具體操作是打開http://<IP>/certsrv,需要授權的賬戶密碼登錄,然後依次點擊: Request a Certificate -> Or, submit an advanced certificate request. -> 填入csr -> Submit。
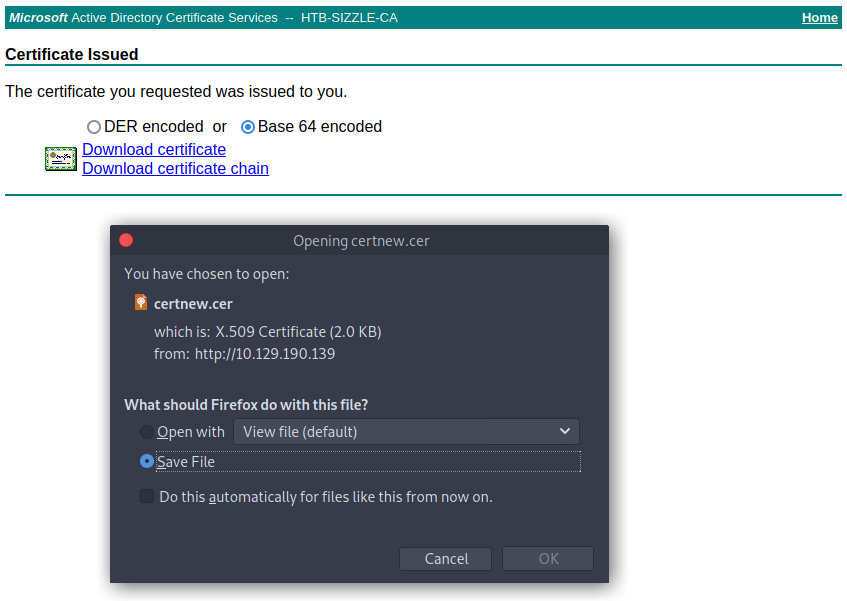
申請成功後你會獲得如下界面:
你可以用openssl x509 -in xxx.cer -text來查看該證書的内容:
$openssl x509 -in certnew.cer -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
69:00:00:00:16:f5:b3:01:a7:67:a5:b4:87:00:00:00:00:00:16
Signature Algorithm: sha256WithRSAEncryption
Issuer: DC = LOCAL, DC = HTB, CN = HTB-SIZZLE-CA
Validity
Not Before: Dec 29 05:19:14 2022 GMT
Not After : Dec 29 05:19:14 2023 GMT
Subject: DC = LOCAL, DC = HTB, CN = Users, CN = amanda
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:c9:2c:af:4b:d0:35:c7:ba:00:49:7b:82:2c:ef:
52:d3:d0:95:e8:71:59:a9:cc:4c:27:60:7e:12:33:
6c:f5:a5:55:54:37:48:f0:d7:8c:05:75:4f:53:a0:
07:02:3b:39:ad:01:0e:24:de:9f:19:9b:c2:96:6f:
eb:0c:2b:9e:18:27:e5:5b:0f:30:59:30:85:16:b9:
1c:10:ef:2c:67:cb:f7:d1:c2:7c:39:c0:b5:0e:43:
95:1c:7f:58:15:3f:e0:5a:fd:b0:18:ad:42:35:5a:
77:97:39:67:7e:60:9d:90:ae:44:b5:49:d6:46:d4:
1d:06:a3:69:7f:97:55:5a:fb:56:e2:9d:90:e5:bb:
42:fe:de:1f:f5:b3:01:a1:d4:96:50:8d:4c:76:81:
1c:4b:b1:a4:ff:42:08:8c:d4:e4:e9:11:f4:7e:50:
d7:71:56:91:00:b5:56:a4:f6:2a:fc:54:1a:f4:27:
8a:04:00:81:18:c5:72:2d:49:f4:cc:cc:55:a9:7c:
7c:3b:e2:3c:4b:42:1c:2e:08:b6:ef:73:cb:d1:14:
a2:f3:2c:36:f0:7e:68:7e:3c:e1:29:16:c7:dc:73:
1f:4d:74:6d:34:5d:56:2f:b5:37:84:de:96:6d:32:
63:27:43:2f:09:81:cf:fb:b8:cb:ac:cc:49:77:08:
7f:61
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
1E:00:96:4E:83:1A:17:5E:54:C7:EA:CA:43:90:82:2C:73:0B:7E:85
X509v3 Authority Key Identifier:
keyid:40:06:E4:54:B3:37:98:BC:22:2E:0E:19:36:0A:18:A0:B1:DE:0B:8A
X509v3 CRL Distribution Points:
Full Name:
URI:ldap:///CN=HTB-SIZZLE-CA,CN=sizzle,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=HTB,DC=LOCAL?certificateRevocationList?base?objectClass=cRLDistributionPoint
Authority Information Access:
CA Issuers - URI:ldap:///CN=HTB-SIZZLE-CA,CN=AIA,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=HTB,DC=LOCAL?cACertificate?base?objectClass=certificationAuthority
1.3.6.1.4.1.311.20.2:
...U.s.e.r
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
Microsoft Encrypted File System, E-mail Protection, TLS Web Client Authentication
X509v3 Subject Alternative Name:
othername:<unsupported>
S/MIME Capabilities:
......0...+....0050...*.H..
..*.H..
Signature Algorithm: sha256WithRSAEncryption
5f:29:d9:d1:f2:b0:2e:8d:fa:90:79:33:9b:0d:4a:9a:cf:ba:
79:17:4a:80:b1:dc:3e:97:7e:78:1a:ae:95:ea:75:86:e8:d8:
14:85:67:a3:92:23:a7:50:69:02:70:14:75:25:2a:32:46:b8:
cd:0a:02:76:75:5d:de:55:af:e0:8e:2a:bb:7c:98:ed:1d:67:
54:2b:dc:90:74:cb:41:3b:a6:97:19:bd:53:7f:c6:21:ac:c4:
52:c3:05:4f:c9:48:f4:90:e1:d3:d8:b1:37:0a:b0:fb:c5:f9:
9f:b7:f9:21:66:20:f4:6d:3c:d7:6d:eb:ec:3c:ed:03:c7:5a:
2e:48:eb:83:b8:c9:02:54:7d:2d:56:83:87:e0:e0:c6:11:18:
35:cf:76:3f:c9:14:fc:98:c5:45:6d:67:0d:e7:64:b7:4a:fc:
f4:85:07:df:81:6b:2e:d3:d9:a2:94:01:2e:e7:db:51:36:e4:
90:e6:bc:0c:26:31:f1:23:27:45:0f:ea:12:fb:52:8f:c4:d4:
92:e3:33:4a:42:64:62:86:90:38:e0:57:ca:f8:43:1d:29:a2:
ac:37:ce:cb:c8:41:1a:43:91:54:af:9b:eb:db:e5:4d:a6:ac:
96:56:a4:91:16:ec:46:d8:c6:c5:73:d2:c1:ee:e7:30:a5:7e:
82:3e:c2:2e
-----BEGIN CERTIFICATE-----
MIIFtjCCBJ6gAwIBAgITaQAAABb1swGnZ6W0hwAAAAAAFjANBgkqhkiG9w0BAQsF
ADBEMRUwEwYKCZImiZPyLGQBGRYFTE9DQUwxEzARBgoJkiaJk/IsZAEZFgNIVEIx
FjAUBgNVBAMTDUhUQi1TSVpaTEUtQ0EwHhcNMjIxMjI5MDUxOTE0WhcNMjMxMjI5
MDUxOTE0WjBNMRUwEwYKCZImiZPyLGQBGRYFTE9DQUwxEzARBgoJkiaJk/IsZAEZ
FgNIVEIxDjAMBgNVBAMTBVVzZXJzMQ8wDQYDVQQDEwZhbWFuZGEwggEiMA0GCSqG
SIb3DQEBAQUAA4IBDwAwggEKAoIBAQDJLK9L0DXHugBJe4Is71LT0JXocVmpzEwn
YH4SM2z1pVVUN0jw14wFdU9ToAcCOzmtAQ4k3p8Zm8KWb+sMK54YJ+VbDzBZMIUW
uRwQ7yxny/fRwnw5wLUOQ5Ucf1gVP+Ba/bAYrUI1WneXOWd+YJ2QrkS1SdZG1B0G
o2l/l1Va+1binZDlu0L+3h/1swGh1JZQjUx2gRxLsaT/QgiM1OTpEfR+UNdxVpEA
tVak9ir8VBr0J4oEAIEYxXItSfTMzFWpfHw74jxLQhwuCLbvc8vRFKLzLDbwfmh+
POEpFsfccx9NdG00XVYvtTeE3pZtMmMnQy8Jgc/7uMuszEl3CH9hAgMBAAGjggKW
MIICkjAdBgNVHQ4EFgQUHgCWToMaF15Ux+rKQ5CCLHMLfoUwHwYDVR0jBBgwFoAU
QAbkVLM3mLwiLg4ZNgoYoLHeC4owgcgGA1UdHwSBwDCBvTCBuqCBt6CBtIaBsWxk
YXA6Ly8vQ049SFRCLVNJWlpMRS1DQSxDTj1zaXp6bGUsQ049Q0RQLENOPVB1Ymxp
YyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24s
REM9SFRCLERDPUxPQ0FMP2NlcnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9v
YmplY3RDbGFzcz1jUkxEaXN0cmlidXRpb25Qb2ludDCBvQYIKwYBBQUHAQEEgbAw
ga0wgaoGCCsGAQUFBzAChoGdbGRhcDovLy9DTj1IVEItU0laWkxFLUNBLENOPUFJ
QSxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25m
aWd1cmF0aW9uLERDPUhUQixEQz1MT0NBTD9jQUNlcnRpZmljYXRlP2Jhc2U/b2Jq
ZWN0Q2xhc3M9Y2VydGlmaWNhdGlvbkF1dGhvcml0eTAXBgkrBgEEAYI3FAIECh4I
AFUAcwBlAHIwDgYDVR0PAQH/BAQDAgWgMCkGA1UdJQQiMCAGCisGAQQBgjcKAwQG
CCsGAQUFBwMEBggrBgEFBQcDAjArBgNVHREEJDAioCAGCisGAQQBgjcUAgOgEgwQ
YW1hbmRhQEhUQi5MT0NBTDBEBgkqhkiG9w0BCQ8ENzA1MA4GCCqGSIb3DQMCAgIA
gDAOBggqhkiG9w0DBAICAIAwBwYFKw4DAgcwCgYIKoZIhvcNAwcwDQYJKoZIhvcN
AQELBQADggEBAF8p2dHysC6N+pB5M5sNSprPunkXSoCx3D6XfngarpXqdYbo2BSF
Z6OSI6dQaQJwFHUlKjJGuM0KAnZ1Xd5Vr+COKrt8mO0dZ1Qr3JB0y0E7ppcZvVN/
xiGsxFLDBU/JSPSQ4dPYsTcKsPvF+Z+3+SFmIPRtPNdt6+w87QPHWi5I64O4yQJU
fS1Wg4fg4MYRGDXPdj/JFPyYxUVtZw3nZLdK/PSFB9+Bay7T2aKUAS7n21E25JDm
vAwmMfEjJ0UP6hL7Uo/E1JLjM0pCZGKGkDjgV8r4Qx0poqw3zsvIQRpDkVSvm+vb
5U2mrJZWpJEW7EbYxsVz0sHu5zClfoI+wi4=
-----END CERTIFICATE-----
這樣子你就獲得了private key amanda.key 和 public key certnew.cer 這兩個密鑰文件。
Using key files to connect winrm over https (5986)
接下來就是用上面那兩個文件去連接 winrm over https.
$evil-winrm -S -c certnew.cer -k amanda.key -i 10.129.190.139
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
Enter PEM pass phrase:
*Evil-WinRM* PS C:\Users\amanda\Documents> whoami
htb\amanda
Conclusion
這是一個很常見的手法,可以説基本上比較偏向于真實的滲透手法。
References
Comments
Post a Comment